 If you are a regular reader of RxTrace but you still haven’t read Fortune Magazine’s recent article, “Drug Theft Goes Big” by Katherine Eban, then I suggest that you stop reading this essay right now and spend the next 15 minutes absorbing her article carefully. And then return here for my analysis. It’s that good and that important.
If you are a regular reader of RxTrace but you still haven’t read Fortune Magazine’s recent article, “Drug Theft Goes Big” by Katherine Eban, then I suggest that you stop reading this essay right now and spend the next 15 minutes absorbing her article carefully. And then return here for my analysis. It’s that good and that important.
Many of you will remember Katherine Eban as the author of the excellent book “Dangerous Doses, A True Story of Cops, Counterfeiters and the Contamination of America’s Drug Supply”. See my comments on the book here where I point out that a lot has changed since the events that are documented so well in the book.
The new Fortune article is a great update on what drug supply chain criminals have been up to since “Dangerous Doses” was published back in 2005. The greatest thing about the article is that it contains one answer to the question that is on the minds of so many people in the industry:
HOW COULD ILLEGITIMATE DRUGS END UP IN THE LEGITIMATE SUPPLY CHAIN?
I wondered about this myself in my recent essay “Do We Even Need To Mandate Drug Pedigrees Anymore?”. But this new article shines a light on one explanation—based on the work of a seasoned investigative reporter—of how this allegedly happened in the instance of some of the Levemir that was stolen back on February 5, 2009. We can use this explanation to figure out how a modern pedigree model might have worked to detect the stolen drugs in the supply chain before they could cause harm to patients.
Let’s construct a hypothetical sequence of events that matches the sequence that Eban’s article describes in her section titled “From Heist to Pharmacists”. That way we can dispense with company names and we won’t have to worry about discussing something that is probably still under investigation and will likely result in future criminal charges.
We know that the drug was manufactured and it was stolen in North Carolina while it was en-route from the manufacturer (M) to some destination. Eban describes how some smaller quantity of drugs that matched the NDC and lot of the drugs that had been stolen were delivered to a licensed wholesaler (W1) in South Carolina five days later.
(As an interesting aside, here is a Google Map that shows a driving route between the town where the real drugs were stolen and the town where the first wholesaler received drugs of the same description as documented by Eban, only 150 miles away. It’s very interesting, but it’s not really important to our analysis of the hypothetical sequence of events.)
W1 quickly resold these drugs to another licensed wholesaler (W2). W2 then sold part of its stock to a third licensed wholesaler (W3) in Maryland. W2 supplied W3 with a “phony pedigree” that inaccurately indicated the drugs had been supplied by a well known national wholesaler.
I use quotes around the phrase “phony pedigree” because that’s what Eban calls it, but that phrase gives the concept of “pedigree” a bad connotation. One might ask, “What good are drug pedigrees if they can be faked so easily?”.
WHAT GOOD ARE DRUG PEDIGREES IF THEY CAN BE FAKED SO EASILY?
A quick check of the state pedigree regulation map posted by the Healthcare Distribution Management Association (HDMA) shows that neither North Carolina nor South Carolina have any kind of pedigree regulation. Coincidence? Maybe, but because neither W1, W2 nor W3 appear to have been Authorized Distributors of Record (ADR’s) for the drug in question, these drug sales should have fallen under the pedigree requirements of the federal Prescription Drug Marketing Act (PDMA). Even with the court ordered stay in 2006 of part of those requirements, it seems that some kind of pedigree should have been required in each of these sales transactions.
But as Eban discovered in her investigation, only the W2 to W3 transaction apparently included some kind of pedigree. That transaction occurred between South Carolina (W2) and Maryland (W3). According to the HDMA’s map, Maryland has a pedigree regulation. Hmmm. Interesting. But it didn’t help because the pedigree was allegedly forged to look legitimate.
Almost certainly, the pedigree that was supplied by W2 would have been a paper pedigree. A paper pedigree is about as easy to forge as a note from your mother excusing you from gym class, but it is legal in every state that currently requires a pedigree for drug sales of this kind. The regulatory acceptability of a paper pedigree is little more than an invitation to criminals to make them up. Most tragic of all, they lend an undeserved impression of legitimacy to this kind of transaction. W3 apparently complied with Maryland’s pedigree law. That is, they apparently received a pedigree along with the drugs. But even so, patients were harmed later. The pedigree didn’t do its job of protecting patients.
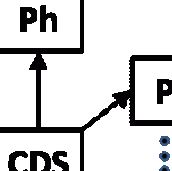
Continuing with the story, W3 sold part of their stock to a chain drug store (CDS) based in Ohio. Eban doesn’t mention if a pedigree was provided with the sale, but Ohio is another state that has no pedigree regulation. CDS apparently distributed these drugs to their pharmacies (Ph) in at least four states where they were later found on pharmacy shelves, but not before at least two of their customers had life-threatening adverse reactions.
WHAT DOES THIS HYPOTHETICAL SEQUENCE OF EVENTS TELL US ABOUT PEDIGREE MODELS?
We have to remember that the drugs in the real story were not serialized. So unless every unit in the entire lot that the manufacturer produced was stolen, it is not possible to say that the drugs that were allegedly found to have caused adverse events were definitely the units that were stolen. That’s why unit-level serialization is a given in any future pedigree model. There’s really no question about it.
I’ve already pointed out that paper pedigrees are worthless for protecting patients. Because they can be forged so easily and the forgeries are so hard to detect, legitimate buyers of illegitimate drugs may accept them and feel confident that the drugs are real. At least these forged paper pedigrees can be used later to help discover who the bad guys are. That’s why investigators would rather have a forged pedigree than none at all. At least they can use the forgery to prosecute the bad guys. The forgery becomes obvious only after a time-consuming investigation.
But shouldn’t pedigrees help protect patients? Shouldn’t they help legitimate supply chain members detect when they are being sold illegitimate products at the time of the sale so they can confidently refuse to buy them and notify the authorities right away? The paper pedigree in our hypothetical story didn’t do that because it couldn’t. A pedigree model is only as protective as the buyer’s ability to validate pedigrees quickly, efficiently and reliably. Paper pedigrees with hand written signatures fail all of those tests.
Now let’s assume that every sale from W1 through CDS included the passing of an electronic pedigree that would be capable of being validated quickly, efficiently and reliably. But that’s still not enough. Even electronic pedigrees can be forged. The difference is that forgeries of electronic pedigrees should be very easy to detect—if the pedigree model includes that feature (not all do).
But that capability alone won’t automatically translate into every legitimate company in the supply chain validating every pedigree. Electronic pedigree validation will still take some amount of CPU time, even if that process is quick, efficient and reliable. If companies don’t have to check the validity of pedigrees, many probably won’t bother. In that case, even with a pedigree model that would be capable of easily detecting a forgery, patients could still be harmed if the pedigrees aren’t checked.
Should companies be required to check every electronic pedigree for validity on receipt? If every recipient had checked an electronic pedigree in our hypothetical sequence, the sequence would have stopped at W1 because they would have easily found that the pedigree they were given was forged. The thief could not have constructed a pedigree without forging the necessary record that only M could have produced. All W1 would have needed to do is check the pedigree and the forgery would have failed validation.
Even if W1 had skipped pedigree validation, the next sale to W2 would have provided another opportunity to detect the forged M record. The sale to W3 provided another opportunity and the sale to CDS another. With the combination of serialization, an electronic pedigree model with the right features and each recipient validating each pedigree they receive, this hypothetical sequence of sales would have provided at least four opportunities to detect that the product was illegitimate before it was ever given to patients. The first recipient to actually validate the pedigree would have detected the forgery and the stolen drug would have been stopped right there.
I am fascinated by the results of Eban’s investigation. Can you see any other lessons from either the real or the hypothetical sequence?


Dirk – Very good analysis – as usual. Interesting case – which seems to dovetail to the track and trace – authentication model suggested by the FDA in February.
I think the moral of all of these situations is that there is no fool-proof system. Criminals will emerge smart enough to forge e-pedigrees, RFID tags or anything else used to serialize. As Eban points out, there is enough money in this to evidentially make it worth the risk for the criminals.
The important thing for the industry and regulators to decide is how best to keep “bad” drugs out of the hands of consumers. Period – and in the most efficient way possible, so other afford ability and supply problems don’t emerge out of good intentions. The more complicated the system, I believe, the more vulnerable pieces of it will be to attack.
By the way – how do you believe that detection schema for forged e-pedigrees would work?
Brian,
Thanks for your comments. I agree with your point about the importance of avoiding a system that will result in higher costs and constrained supply. However I’m not convinced that a consumer-based authentication system is what we should be striving for here in the U.S.. I will try to explore that concept and others in a future essay. The main point I hope to make is that different pharma supply chains around the world have different problems, and those different problems require different solutions. Watch for it in the future.
As for the detection of forged ePedigrees, we know that digital signature-based solutions can be used to make any tampering—even a change to a single character—completely obvious and that can be done locally without needing to pull additional information from the internet. When using digital signatures, detecting that a pedigree has been tampered with is quick, efficient and very reliable. See my essay on Digital Signatures for more details. There may be other technical mechanisms that accomplish the same goals even more efficiently.
Dirk.
Great post! Thanks for the insight!
Lessons I learned:
1.) Florida has run the criminals off local streets as seen in Dangerous Doses and apparently into out of the state wholesale criminal activities. Interesting enough: The criminals still live in FL but have to operate outside FL borders. Is this because of FL pedigree?
2.) Pedigree and Serialization has to start from the Manufacturing point. The Manufacturers cannot be exempt from Pedigree/Serialization. Remember, most of these thefts are from the MFG not the distributer.
3.) Some ePedigree models can validate each serialized bottle? Wow! I wonder which models perform this validation tasks and how it works?
4.) Pedigree/Serialization maybe more cost effective than recalls?
5.) Major Incentives for technology development and implementation are needed for all participants in the supply chain. Bottom line is no-one wants to pay for the technology.
Enjoyed your post.
George,
Those are great lessons. Thanks for listing them. Regarding lesson #3 in your list, the GS1 Drug Pedigree Messaging Standard (DPMS) makes use of digital signatures which make them tamper-proof as long as you validate the signatures on receipt. GS1 currently has a group looking at other potential models that would be implemented differently, but all of them would include the a similar ability, one way or another. It’s too early to tell where that effort will end up.
Dirk.